The world of cloud computing is starting to feel like a bustling airport at peak holiday season—endless options, connections everywhere, and plenty of potential turbulence.
For businesses, the multi-cloud landscape mirrors this chaos, with organizations juggling multiple cloud providers to stay agile and scalable.
However, with this flexibility comes a daunting challenge: securing data across these complex environments.
A report by Statista highlights that “76% of organizations use multiple cloud providers for their operations.”
With so much critical data spread across platforms, ensuring robust security measures is no longer a luxury but a necessity.
But don’t just yet hit the panic button!
Though some of the risks listed above in mismanaged data security in multi-cloud architecture are valid, the good news is that these challenges can be dealt with with ease.
With the right strategies, tools, and expertise, businesses can enjoy the best of both worlds: agility without compromising security.
That’s why in this blog, we will look at the best practices for multi-cloud security and solutions for its common challenges to help you keep your cloud data privacy intact, assure compliance, and give peace of mind in treading the ecosystem of multi-cloud.
Let’s dive in!
What is Multi-Cloud Security?

Multi-cloud security involves all-around protection of data and applications located on multiple cloud platforms.
It means establishing a unified security system across the multiple environments within your cloud ecosystem-not much different from the way a smart home security system has been installed in your home to guard different entry points of the house with various types of sensors.
That would mean that from AWS to Google Cloud and so on, the security framework will safeguard the data of an organization.
While this provides greater flexibility and redundancy, security policies, access controls, and monitoring systems must be carefully coordinated to maintain consistent protection across all platforms.
Why Do You Need to Use a Multi-Cloud Strategy?

In the digital landscape today, a multi-cloud strategy has become as basic as portfolio diversification to reduce risk while increasing returns. This will have the added effect of organizations being able to exploit the various strengths of a variety of cloud providers and avoid vendor “lock-in.”
Consider also how each is superior to the others on different competencies: for example, one may provide better database services, while another provides cheaper storage.
By strategically distributing workloads across multiple providers, organizations can optimize both performance and costs. This flexibility also enhances business continuity; if one provider experiences an outage, critical operations can continue running on other platforms.
After all, downtime is a business’s worst enemy, with a report stating that “downtime can cost businesses approximately $5,000 a minute.”
Additionally, a multi-cloud strategy provides significant negotiating power, allowing organizations to secure better pricing and terms by maintaining relationships with multiple providers. This approach ensures both operational resilience and financial efficiency in your cloud infrastructure.
Scenarios When Multi-Cloud Security is Used
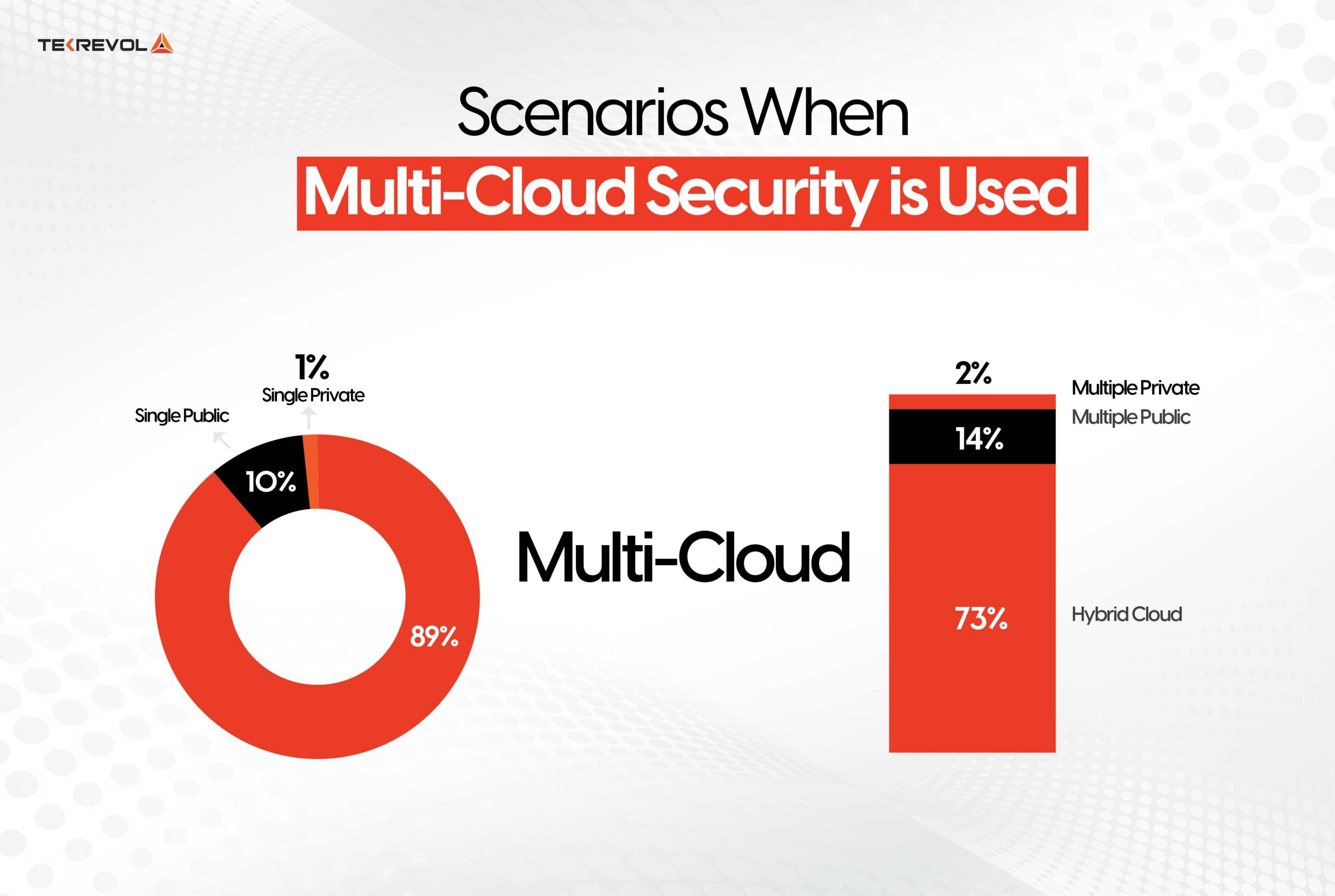
Multi-cloud security has been serving all kinds of purposes and has thus been adopted by enterprises at very high speed. In this respect, the 2024 State of the Cloud report by Flexera says, “89% of enterprises now embrace a multi-cloud strategy, underscoring the growing reliance on multiple cloud providers for scalability and resilience.”
However, the use cases for multi-cloud security include the following:
Disaster Recovery Solutions
Multi-cloud security enables robust multicloud disaster recovery by maintaining synchronized backups across different cloud providers. This approach ensures business continuity during outages, with automated failover systems allowing quick recovery while maintaining data integrity and security protocols.
Data Segmentation
Organizations use multi-cloud security to strategically distribute sensitive data across providers. This segmentation creates natural security boundaries, reducing the impact of potential breaches while allowing different departments to utilize cloud services best suited to their needs.
Regulatory Compliance Management
Multi-cloud security helps organizations meet varying compliance requirements across different regions and industries. By implementing provider-specific security controls and maintaining consistent compliance policies, businesses can effectively manage regulatory obligations while operating in multiple jurisdictions.
Development and Testing Environments
Development teams leverage multi-cloud security to create isolated testing environments that mirror production settings. This setup enables secure testing of applications and updates across different cloud platforms while protecting sensitive production data.
Advanced Threat Detection
Hybrid and multicloud security systems provide comprehensive threat monitoring across platforms, integrating various security tools and AI-powered detection systems. This multi-layered approach works faster in identifying potential threats, with better protection against complex cyberattacks.
Key Components of a Multi-Cloud Security Architecture
The three key components of multi-cloud security architecture are as follows:
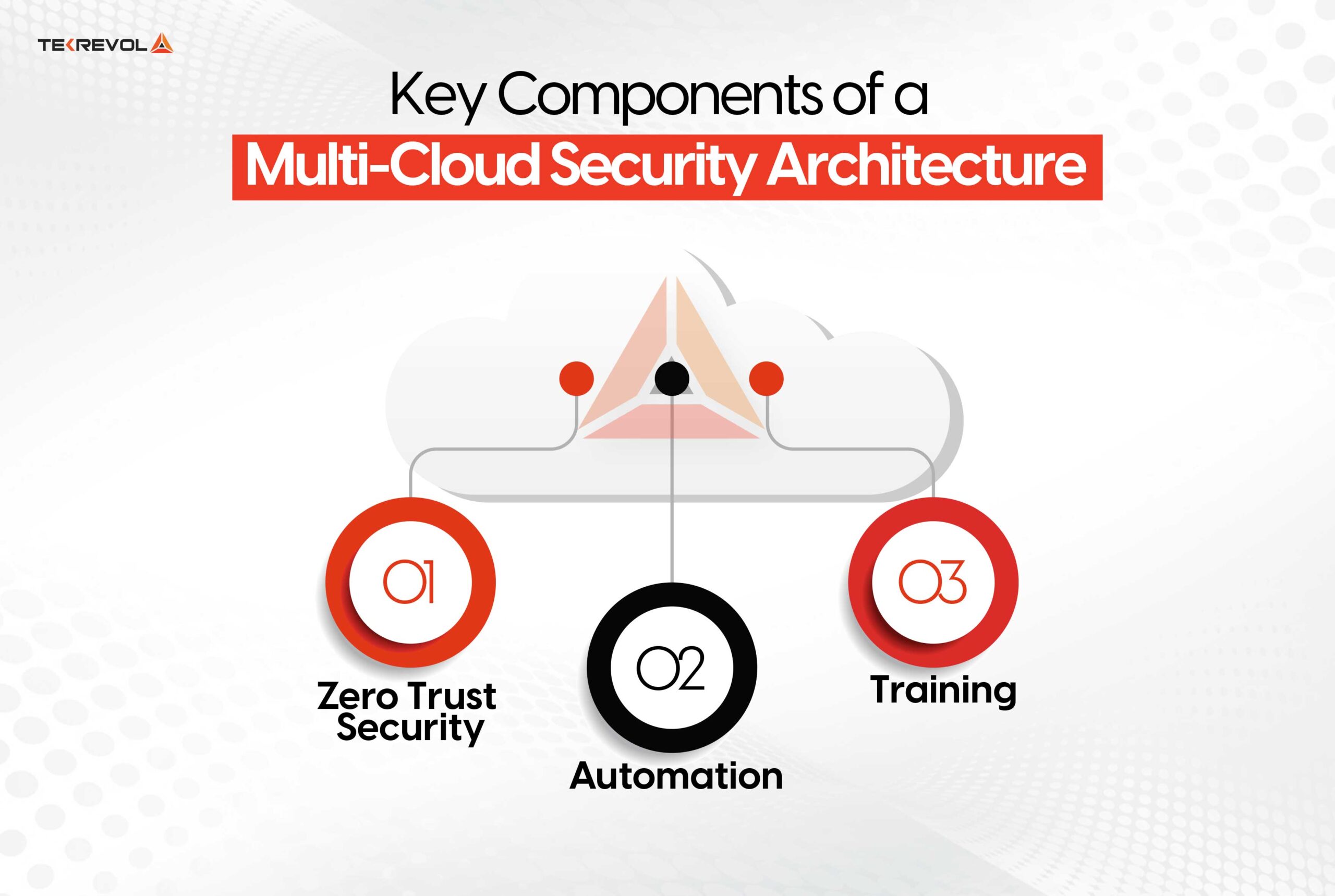
Zero Trust Security
With strict verification of every user, device, and application through role-based access controls, real-time monitoring, and behavior analytics, this comprehensive security model keeps up with the business in all cloud environments through a “never trust, always verify” approach.
Regular authentication checks and limited access permissions reduce potential security breaches.
Automation
Automated security tools manage configuration settings, deploy security patches, and respond to threats across multiple cloud platforms simultaneously.
This reduces human error risks while ensuring consistent security implementation. Automation also enables rapid incident response, continuous compliance monitoring, and standardized security protocols across all cloud environments.
Training
Comprehensive security training programs equip teams with essential skills for managing multi-cloud environments securely. Training covers platform-specific security features, compliance requirements, and threat detection protocols.
Also, regular updates ensure staff stays current with emerging threats and security best practices while maintaining expertise across different cloud platforms.
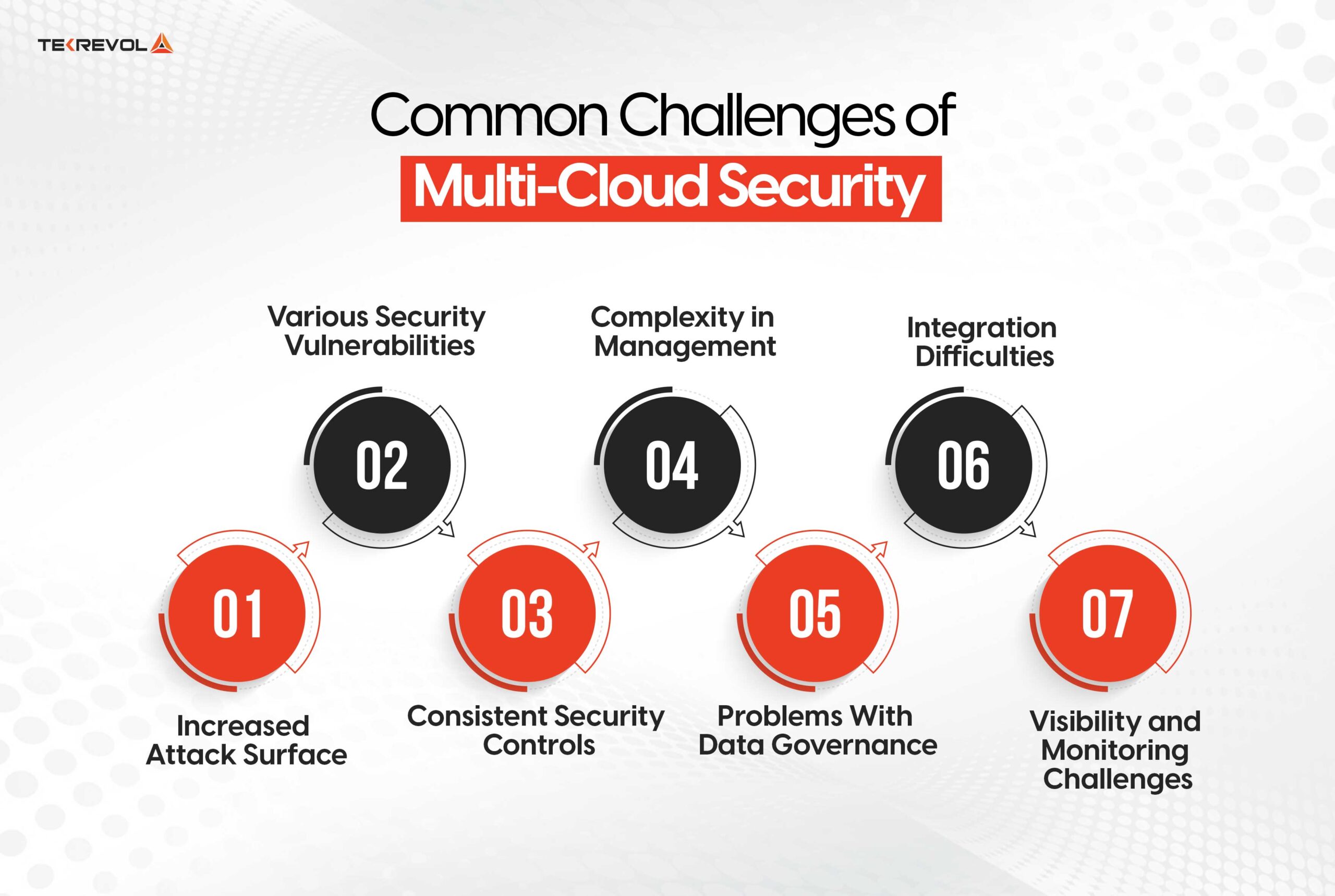
Common Challenges of Multi-Cloud Security
No multi-cloud architecture is without its problems. More so, as the Cost of a Data Breach report by IBM states, “The estimated total cost of a data breach was around US$4.45 million worldwide.” So, that itself is more than a good reason to know there are a few challenges with multi-cloud security.
Therefore, the most common challenges of multi-cloud security are as follows:
Increased Attack Surface:
Multiple cloud environments significantly expand potential entry points for cybercriminals. Each additional platform introduces new vulnerabilities requiring constant monitoring and protection. This expanded attack surface demands more sophisticated security measures and increases the complexity of threat detection and response protocols.
Various Security Vulnerabilities
Different cloud providers present unique security challenges and weaknesses in their architectures. Managing these varied vulnerabilities requires specialized knowledge of each platform’s security features and limitations. Organizations must develop comprehensive strategies to address platform-specific risks while maintaining consistent security standards.
Consistent Security Controls:
Maintaining uniform security policies across different cloud platforms creates significant operational challenges. Each provider offers varying security features and capabilities, making it difficult to implement standardized controls. Organizations must bridge these gaps while ensuring consistent protection across all environments.
Complexity in Management:
Coordinating security measures across multiple platforms significantly increases operational complexity. This requires additional expertise, resources, and sophisticated management tools. Teams must navigate different interfaces, security protocols, and compliance requirements while maintaining effective security oversight.
Problems With Data Governance
Managing data compliance and security policies across various cloud environments presents significant governance challenges. Organizations must ensure consistent data handling practices, maintain regulatory compliance, and implement unified access controls while dealing with different provider-specific governance tools.
Integration Difficulties
Connecting security tools and processes between different cloud platforms creates substantial technical challenges. Organizations face compatibility issues, API integration problems, and data synchronization difficulties. These integration challenges can impact security effectiveness and operational efficiency.
Visibility and Monitoring Challenges
Maintaining comprehensive security visibility across multiple cloud environments complicates threat detection and response. Organizations struggle to create unified monitoring systems that provide real-time insights across all platforms while ensuring consistent incident reporting and analysis capabilities.
How to Tackle Those Multi-Cloud Security Challenges?
Managing security across multiple cloud platforms requires a well-orchestrated approach to address unique challenges while maintaining operational efficiency. The complexity of multi-cloud environments demands special attention to potential security gaps that can emerge when integrating different cloud services.
- One critical aspect is understanding and managing the varying shared responsibility models across cloud providers. Each provider has distinct security boundaries and responsibilities, making it essential for organizations to map out their security obligations. This includes identifying where provider security measures end and where organizational controls need to begin.
- Misconfigured cloud resources pose significant risks in multi-cloud environments. Organizations must vigilantly monitor and review cloud configurations across all platforms. This includes carefully managing network settings, access points, and default configurations that could create security vulnerabilities if left unchecked.
- Visibility challenges can be particularly daunting when working across multiple clouds. Organizations need to establish comprehensive monitoring systems that can track resource usage and security events across all cloud platforms simultaneously. This holistic view helps identify potential threats that might exploit gaps between different cloud environments.
- Managing the expanded attack surface in multi-cloud environments requires a strategic approach to security. Each additional cloud service introduces new potential entry points for attackers. Organizations must carefully assess the security implications of each new cloud service and implement appropriate controls without duplicating efforts or creating conflicting security measures.
- Data governance becomes more complex when data flows between different cloud environments. Organizations need to establish clear policies for data movement, storage, and processing across clouds while ensuring compliance with various regional and industry-specific regulations.
10 Best Practices for Ensuring Data Security in Multi-Cloud Environments
There is no shortage of multi-cloud data security best practices. However, we have picked out the best ten of them that you need to use to
protect your data in multi-cloud architectures. Therefore, these practices are as follows:
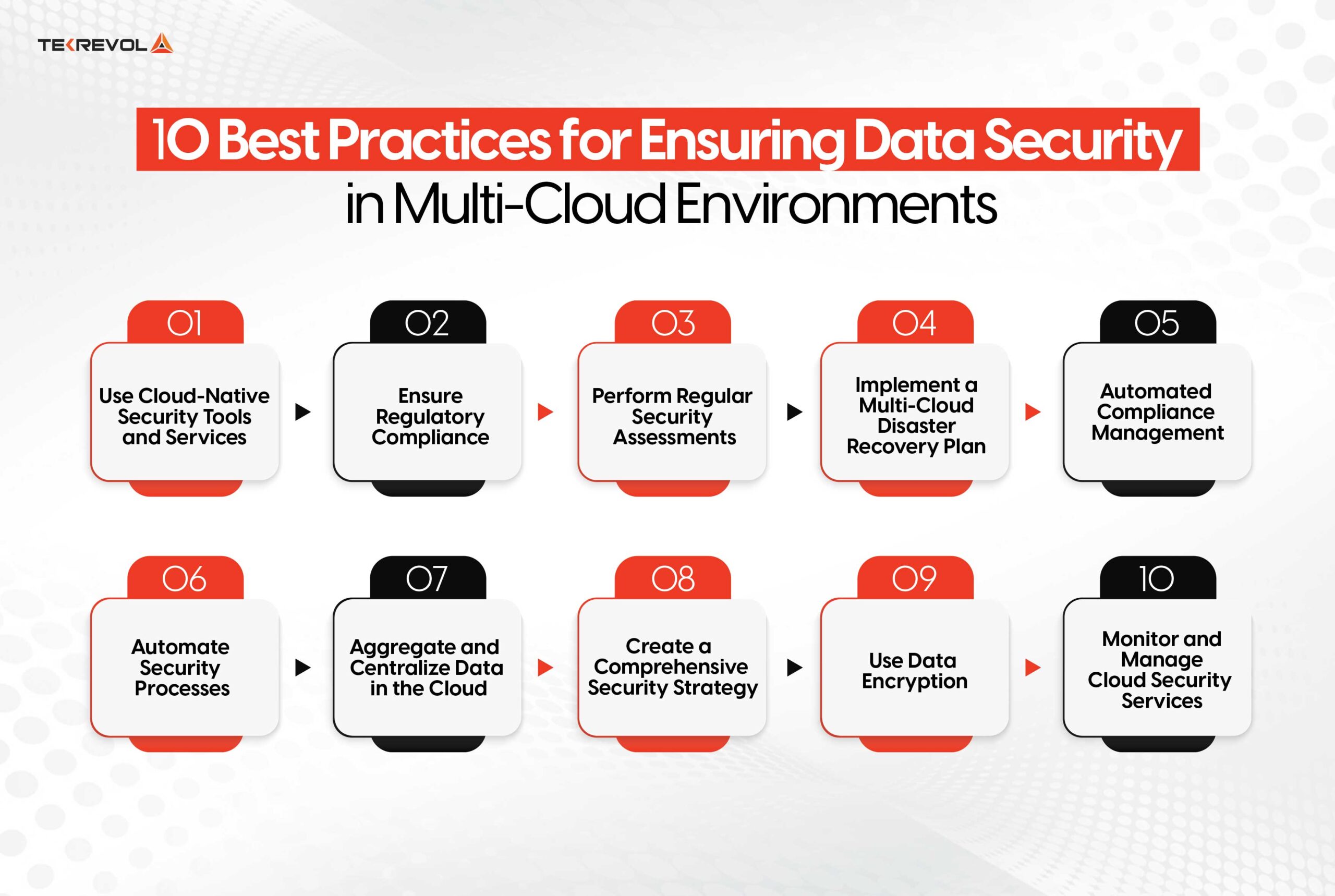
Use Cloud-Native Security Tools and Services
Leverage the power of built-in security tools offered by your cloud providers. These tools are designed specifically for their platforms, ensuring seamless integration and optimized protection.
From threat detection to identity management, cloud-native tools simplify your security efforts while staying up to date-with the latest defenses. Think of them as your cloud’s personal security team, always on duty.
Ensure Regulatory Compliance
Compliance is not just a way to avoid fines. Instead, it is about building trust. Learn what regulations apply to your industry, then make sure your multi-cloud setup meets the standards.
Be it GDPR, HIPAA, or CCPA, compliance with these frameworks not only keeps sensitive data secure but also builds your brand. Pro tip: Audits and automated tools keep compliance painless.
Perform Regular Security Assessments
The best practice is to never wait until a breach to test your defenses. Run frequent security assessments to find weaknesses before the hackers do.
Think of it as having a check-up for the health of your multi-cloud, scanning for weak spots, and ensuring all systems are in top shape. That’s how you keep your head above water in these changing times.
Implement a Multi-Cloud Disaster Recovery Plan
Prepare for the unexpected by having a disaster recovery plan tailored to your multi-cloud setup. This ensures that even if one cloud fails, your data and operations stay intact.
From data backup solutions for multicloud to failover systems, your recovery plan is your safety net in a storm—keeping downtime minimal and business continuity intact.
Automated Compliance Management
Why stress over compliance when automation can handle it? You can monitor, report, and maintain compliance with regulatory standards continuously using automated tools.
To put it in other words, it’s like a compliance assistant that never sleeps or sleeps with one eye open, always on the look for issues and flagging risks to keep your multicloud environment on the right side of the law.
Automate Security Processes
Manual security checks are so last decade. Automate routine activities like patch management, threat detection, and access control to free the manpower to think about bigger-picture strategies.
Automation not only saves time but also reduces the number of human errors, which sharpens your defenses and makes your operations more efficient. Plus, it frees your team for much-needed work on more critical strategy projects.
Aggregate and Centralize Data in the Cloud
Spread-out data can lead to chaos. Centralize it for better visibility and control. Aggregating data across your multi-cloud environment makes monitoring and securing it easier. Think of it as organizing your wardrobe—when everything’s in one place, it’s easier to manage and protect.
Create a Comprehensive Security Strategy
A piecemeal approach is not good enough. Create a holistic security strategy to protect every part of your multi-cloud-from access control to incident response. In such a big-picture approach, each layer will be covered, and your team will know what to do if something goes wrong.
Use Data Encryption
Data encryption in multicloud is like a bodyguard for your data: even if the data falls into the wrong hands, it keeps sensitive information safe. Encrypt data at rest, in transit, and wherever it resides in your multi-cloud environment. It’s simple, yet one of the most powerful ways to keep prying eyes at bay.
Monitor and Manage Cloud Security Services
Security isn’t a set-it-and-forget-it deal. Regularly monitor your cloud services to spot anomalies, address vulnerabilities, and stay ahead of threats. Use managed services or dedicated tools to keep everything in check. Think of it as keeping an eye on your home—better safe than sorry!
Why Secure Your Data in Multicloud Architectures With Tekrevol?
Scalability and efficiency are major concerns in the fast-moving digital landscapes, hence the ever-growing reliance on multi-cloud architecture. As the popular Spider-Man quote goes, great flexibility means great responsibility; securing your data across a myriad of platforms might be quite a challenge.
This is where Tekrevol enters the chat.
We offer a comprehensive approach to multi-cloud security, blending bleeding-edge tools with customized strategies for your data protection in multicloud against cyber threats, breaches, and compliance risks.
Be it encryption, automated monitoring, or planning for disaster recovery, Tekrevol ensures every layer of your cloud environment is fortified.
At Tekrevol, our team doesn’t just provide cloud migration solutions but works with you on the ground to know your unique needs to let data stay available with you yet guarded.
With Tekrevol, the cloud is not the only thing you guard but building trust and resilience within business processes. Experience peace of mind with Tekrevol through your journey in multi-clouds!
Closing Thoughts
When the backbone of modern business operations seems to revolve around multi-cloud architecture, securing your data across diverse platforms hasn’t been more critical lately.
Though the flexibility and scalability in a multi-cloud environment are unmatched, with unique challenges, a very proactive approach is certainly needed toward solutions. To remove the gap between innovation and security, that is when TekRevol steps in.
Our comprehensive approach involves including powerful tools and customized strategies to protect your data against different kinds of threats and non-compliance, which will keep your operations up and running with minimal or no disruption.
From encryption and disaster recovery planning to automated monitoring and centralized management, our solutions are designed to secure every layer of your multi-cloud environment.
When you partner with Tekrevol, you’re not just protecting your data-you’re building a resilient, future-proof foundation for your business.

 752 Views
752 Views February 3, 2025
February 3, 2025