Just when you start enjoying the freedom of accessing your data from any part of the world after you have just moved your business applications to the cloud, that is when you get hit by a cold uppercut thrown like Mike Tyson’s to your jaw. That is when you start having concerns about who else might be accessing that data too.
In today’s digital world, cloud applications are like sky-high office buildings – incredibly convenient, but they need the right security measures to keep the wrong people out. Think of security in your cloud migration solutions as your digital bodyguard, working 24/7 to protect your valuable information floating in the cloud.
And trust me, you’re going to want this protection- with cyber threats evolving faster than your smartphone’s operating system updates, staying secure isn’t just an option anymore, it’s a necessity.
That is the reason cloud application security is in extensive demand. According to a report from Statista, “The revenue in 2024 in the cloud security market was over US$2.05 billion. By the end of 2029, the market will grow at (CAGR) of 26.34% and will be valued at around US$6.60 billion.”
Whether it is a startup taking its baby steps into the cloud, or an enterprise with multiple applications in the cloud, Cloud Security is no longer to be left to the geniuses in the IT department. It’s something that is important and needs to be understood at all levels from the CEO to the intern handling customer data.
That is why, in this guide, we are going to talk about cloud application security, from its challenges to risks and best practices and solutions that will help you sleep better, knowing that your cloud data is well and truly protected. Now let’s dive in without any further ado.
What is Cloud Application Security?

To answer what is cloud application security, think of cloud application security as your digital fortress in the sky. It’s an extended set of policies, technologies, and controls working through the process of securing apps, data, and all infrastructures in the cloud from any form of threats that may be targeted.
Going by analogy, just the same way a housekeeper uses home security to protect his house from intrusion across various entry points, so likewise cloud application security guards up everything from user access up to data transmission and use, including storage and handling.
It’s not just about building walls – it’s about creating an intelligent security ecosystem that can detect, prevent, and respond to threats while keeping your cloud operations running smoothly.
Importance of Cloud Application Security

In today’s digital landscape, cloud application security isn’t just an IT checkbox – it’s your business’s survival kit. Cyber attacks are becoming more and more clever. More so, data breaches result in losses of millions and millions of dollars.
The IBM Cost of a Data Breach Report 2024 supports this fact, as according to it, “The global average cost of a data breach was more than US$ 4.88 million in 2024.”
That is why robust cloud security is all that stands between your data and the threats out there. Think about it: your cloud applications handle customer information, financial data, and business secrets daily.
It is like you are leaving the doors of your digital home wide open if you do not properly secure your information. Also, as regulations like GDPR and CCPA are turning out to be more severe day by day, good security has moved past being just protective to being legally compliant and maintaining customer trust.
Types of Cloud Application Security Solutions
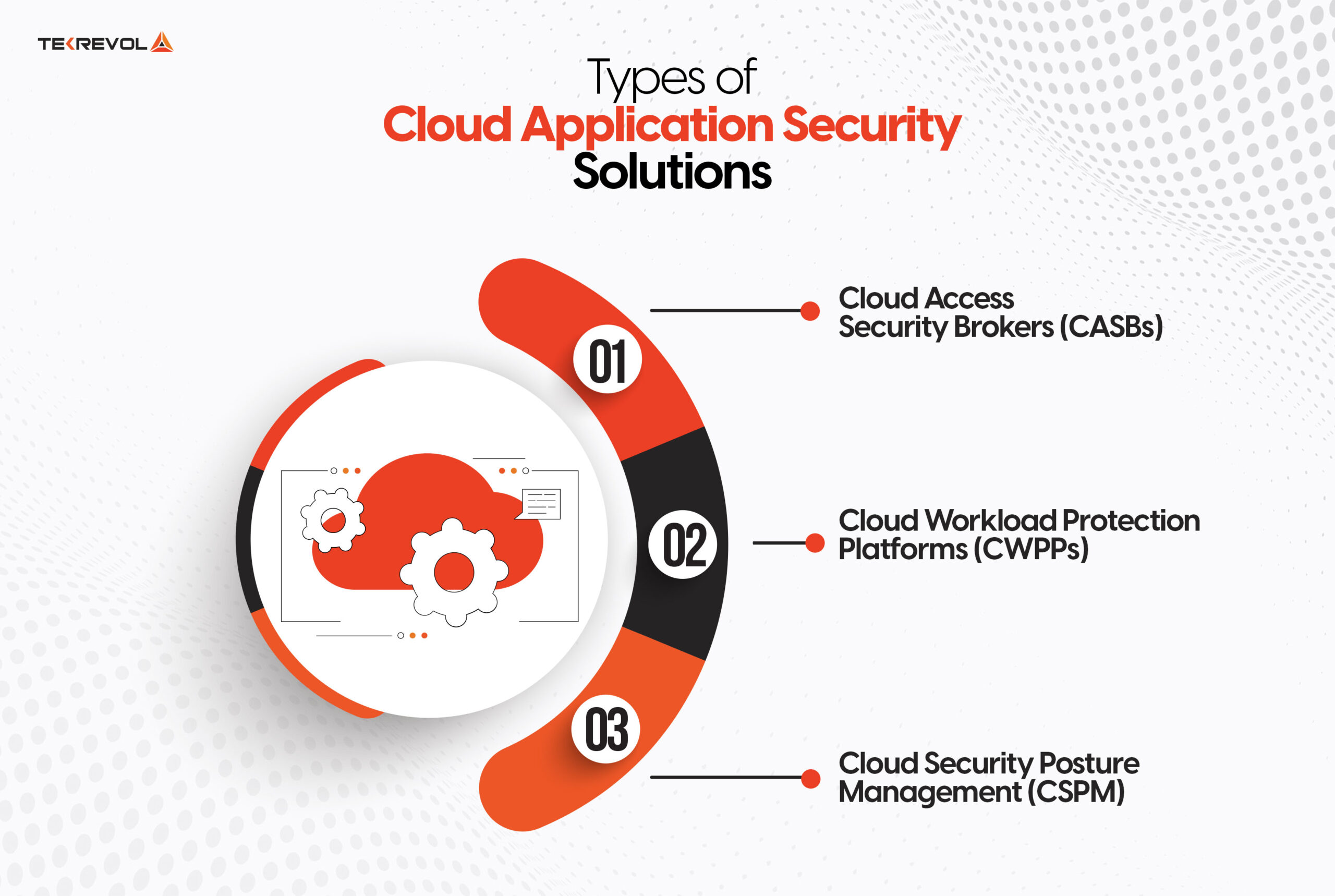
There are various types of cloud application security solutions for securing cloud applications. Each one of these solutions secures cloud applications in a different way and they are as follows:
Cloud Access Security Brokers (CASBs)
Think of CASBs as your cloud security traffic cops! These smart tools sit between your users and cloud services, monitoring all activity and enforcing security policies. They offer visibility into shadow IT, control data access, protection from threats, and compliance- maybe your all-in-one security checkpoint for cloud services.
Cloud Workload Protection Platforms (CWPPs)
CWPPs are a lot like special bodyguards for your cloud workloads. They protect your applications, data, and infrastructure across multiple cloud environments. From container security monitoring to virtual machine protection, CWPPs provide real-time protection and automated threat responses so your workloads are secure wherever they run.
Cloud Security Posture Management (CSPM)
CSPMs are your cloud security health checkers. They run constant scans on your cloud environment for misconfigurations, compliance issues, and security risks. Much like a smart home system that would notify one of the open doors, CSPM solutions find the weak links in your cloud configuration and assist in remediation before hackers can leverage them.
Key Components of Cloud Application Security
There are two main components of application security in cloud computing, and they are as follows:
Regulatory Compliances
Just as restaurants must follow health codes, cloud applications must adhere to specific regulations. From industry to region, the demands range from the GDPR for European data to HIPAA for healthcare. The key to compliance, however, goes beyond not getting fines; it shows a system of structured and secured practices for sensitive information.
Industry Standards
Think of industry standards as the best practices playbook for cloud security. They are a bit like cookbooks written by security experts with battle-tested ways of how to safeguard cloud applications. Such standards as ISO 27001 and SOC 2 provided a framework that allowed an organization to build a really robust Security Program.
Advantages of Using Cloud Application Security
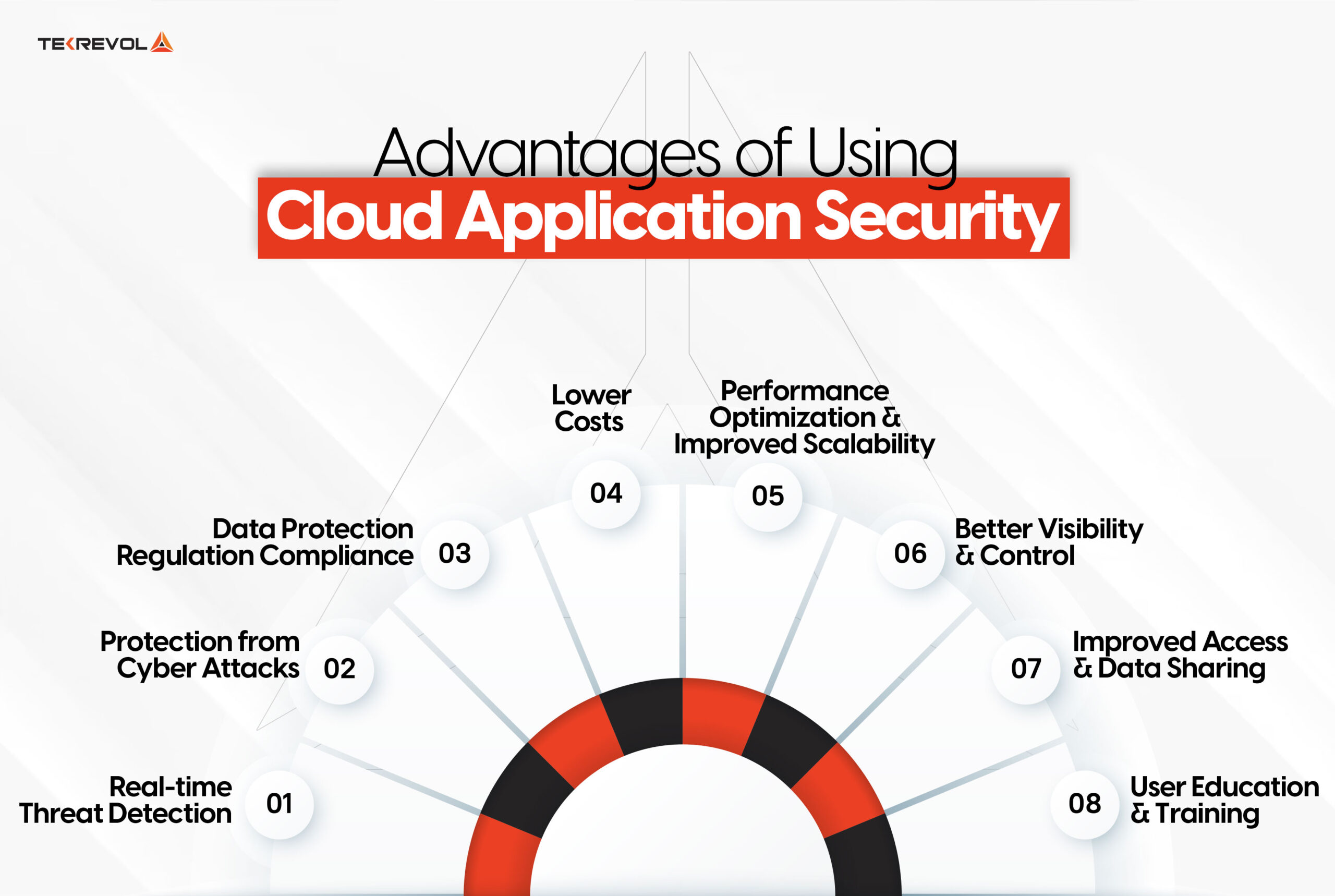
There are a lot of benefits to implementing cloud application security. Not only does it protect cloud data but it also maintains business continuity. So, let’s look what are some other benefits that cloud application security offers:
Real-time Threat Detection
Like a high-tech security camera system, real-time threat detection constantly monitors your cloud environment for suspicious activity. It uses advanced analytics and AI to spot potential threats instantly, allowing your team to respond before minor security incidents become major breaches.
Protection from Cyber Attacks
This acts like your digital immune system, defending against various cyber threats – from ransomware to phishing attempts. It includes multiple layers of security controls, automated threat responses, and advanced filtering systems that work together to keep your cloud applications safe from attackers.
Data Protection Regulation Compliance
Think of this as your security rule book navigator. It helps ensure your cloud setup meets all necessary regulations like GDPR or HIPAA. With built-in compliance tools and automated reporting, staying within legal boundaries becomes less of a headache and more of an automated process.
Lower Costs
Cloud security saves money by preventing breaches or even just automating security processes a block away. Cloud security isn’t exactly cheap, but when all is said and done, it is indeed rather like buying good insurance: you hope that you never have a security incident, but knowing it is there can literally mean the difference between getting busted financially or not.
Performance Optimization and Improved Scalability
Good security doesn’t just protect – it optimizes! Modern cloud security solutions are designed to work efficiently, minimizing the impact on application performance. They scale automatically with your needs, ensuring protection grows alongside your business without creating bottlenecks.
Better Visibility and Control
Like having a control room with monitors showing every corner of your building, cloud security provides comprehensive visibility into your entire cloud environment. You can see who’s accessing what, when, and from where, making it easier to spot and address potential security issues.
Improved Access and Data Sharing
Security doesn’t mean restriction – it means smart control. Modern cloud security solutions make it easy to share data securely, like having a sophisticated digital key system that ensures the right people have the right access at the right time.
User Education and Training
Just as a car’s safety features work best with a trained driver, cloud security works best with educated users. This component focuses on training your team to recognize threats, follow security best practices, and become your first line of defense against security incidents.
Best Practices for Cloud Application Security

There are a lot of best practices for securing cloud applications. However, we have picked out the 11 best of them and they are as follows:
Regularly Backup Data
Think of backups as your digital safety net. Just like keeping copies of important documents, you need to regularly back up your cloud data. Do backups in multiple locations, test your recovery processes, and encrypt your backups. It’s not just a question of having backups. Instead, it is a question of having backups you can trust and restore with speed.
Evaluate Built-In Security
Before diving into third-party security tools, explore what’s already at your disposal. Many cloud platforms come with robust security features built-in, like AWS’s GuardDuty or Azure Security Center. It’s like checking what safety features come with your car before buying additional accessories.
Conduct Security Audits and Assessments
A security audit works just like a routine doctor check-up for your cloud environment. It finds vulnerabilities, compliance gaps, and security weaknesses. You can perform periodic assessments, including penetration testing and vulnerability scanning, to assure the efficacy of your security controls and show areas that require improvement.
Continuous Monitoring and Logging
Like a 24/7 security camera system, continuous monitoring keeps track of everything happening in your cloud environment. Set up comprehensive logging systems that track user activities, system changes, and potential security events. This creates an audit trail that’s invaluable for threat detection and incident investigation.
Use File-Level Encryption
File-level encryption gives a personal safe for each document. You encrypt separate files so that even if unauthorized access to the cloud storage occurs, your important information will not be disclosed to this person. Implement strong encryption algorithms and manage encryption keys carefully.
Identity and Access Management
Consider that it’s as if one is assigning the job of a sophisticated, digital doorman who can know just who should be allowed into what.
Second, provide role-based access control, multi-factor authentication, and periodic access reviews. Also, ensure that users only have the level of access they actually need and make sure such access is cut without further ado where necessary.
Incident Response Planning
Like having a fire evacuation plan, you need a clear strategy for handling security incidents.
Develop detailed response procedures, assign responsibilities, and regularly practice your incident response plan. Include steps for containment, eradication, recovery, and lessons learned.
Strong Credential Policies
Think of credentials as the keys to your digital kingdom. Implement strict password requirements, regular password changes, and multi-factor authentication. Train users about password security and consider using password managers to maintain strong, unique credentials across all accounts.
Securely Transfer Data
Just as you wouldn’t send valuable items through regular mail without insurance, secure your data during transit. You will need to use encrypted connections (SSL/TLS), secure file transfer protocols, and verify the integrity of transferred data. Audit all data transfers and establish various controls to detect and block unauthorized exfiltration of data.
Secure Devices
Every device accessing your cloud applications is a potential entry point. Implement endpoint protection, require device encryption, and establish minimum security standards for all connected devices. Think of it as ensuring every door and window in your security perimeter is properly locked.
Enable Cloud Workload Protection
Like having specialized security guards for different areas, cloud workload protection ensures each component of your cloud infrastructure is properly secured. This includes container security, serverless function protection, and virtual machine monitoring.
Challenges of Cloud Application Security:
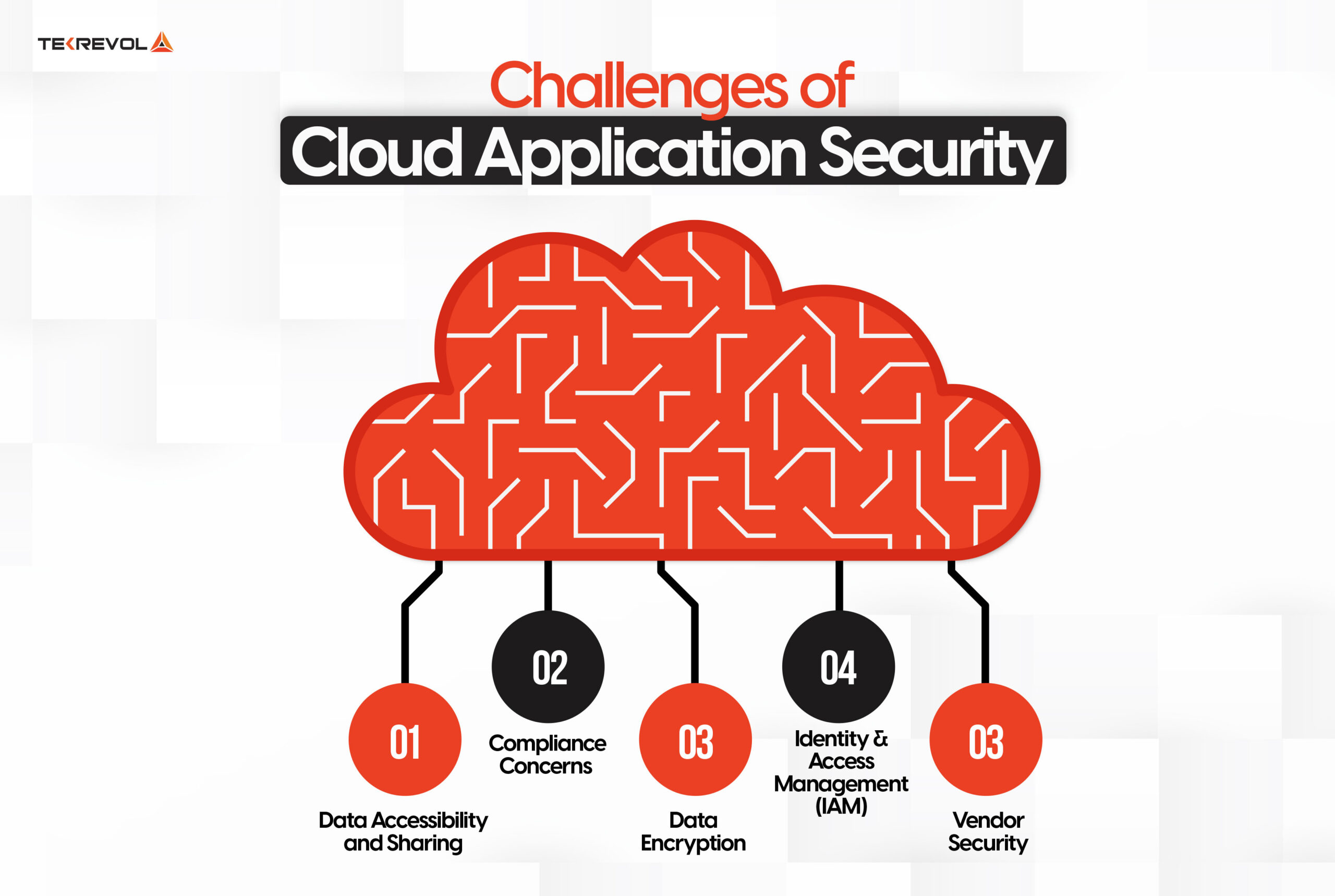
No solution is perfect and cloud Application security is certainly not without its sets of challenges Therefore, let’s look at what these challenges are:
Data Accessibility and Sharing
Balancing easy access with security is like walking a tightrope. Organizations struggle with providing convenient data sharing while preventing unauthorized access. This challenge involves implementing secure sharing methods, controlling data movement, and maintaining visibility over shared resources.
Compliance Concerns
Going through the maze of compliance requirements can be a bit of a hassle. Different regions and industries have different regulations. So, staying compliant while maintaining operational efficiency is challenging, to say the least. It’s like trying to follow different rule books simultaneously while keeping your business running smoothly.
Data Encryption
Managing encryption across cloud environments is complex. Organizations struggle with key management, selection of proper encryption techniques, and complete cloud data encryption its entire life cycle. It is a lot like having many safes with different combinations, which all have to work together flawlessly.
Identity and Access Management (IAM)
Managing user identities and their rights to a variety of cloud services is no different from managing security clearances for a large facility. Challenges faced by an organization include the implementation of consistent access policies, prevention of privilege escalation, and proper authentication across disparate platforms.
That is one of the leading causes of cloud security failures, and Gartner predicts in one report that “Through 2025, 99% of cloud security failures will be the customer’s fault, driven primarily by misconfigurations and improper access management.”
Vendor Security
Relying on cloud vendors adds another layer of security considerations. Organizations must verify vendor security practices, ensure they meet compliance requirements, and maintain visibility into vendor security measures. It’s like trusting someone else to guard part of your valuable assets.
Common Cloud Application Security Threats and How to Address Them
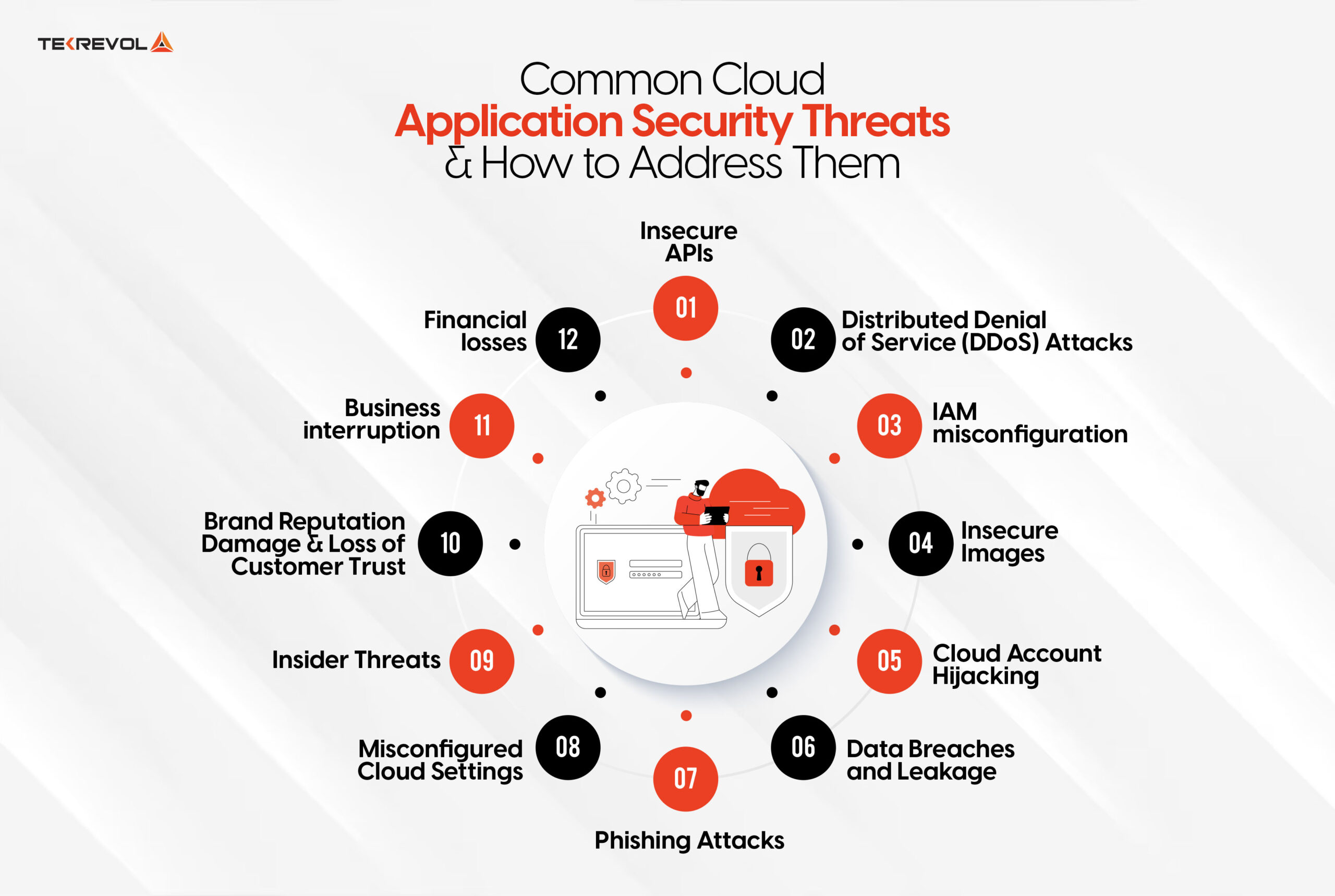
There are a lot of various security risks and threats that cloud application security can face if not dealt with right away. So, let’s look at what these threats are and how to address them to keep cloud data privacy intact:
Insecure APIs
Think of APIs as the doorways to your cloud applications. When they’re not properly secured, it’s like leaving these doors unlocked. Attackers can exploit weak API authentication, inject malicious code, or intercept sensitive data. To protect APIs, implement strong authentication, use API gateways, and regularly test for vulnerabilities.
Distributed Denial of Service (DDoS) Attacks:
Like a mob overwhelming a store entrance, DDoS attacks flood your cloud services with traffic until they crash. These attacks can paralyze your operations and mask other malicious activities. Implement DDoS protection services, traffic filtering, and rate limiting to maintain service availability during attacks.
IAM misconfiguration
IAM misconfiguration is just like giving every single person a master key when all they need is access to a certain room. As per the 2023 Cloud Security Report by Check Point Research, “76% of the organizations experienced at least one cloud security incident in the past year due to misconfiguration (27%) and unauthorized access at 23% identified as leading causes.”
IAM misconfigurations happen when access permissions aren’t properly set up, leading to unauthorized access. Regular audits, the principle of least privilege, and automated policy checking can prevent these security gaps.
Insecure Images
Using vulnerable container images is like building on a shaky foundation. These images might contain outdated software, malware, or security vulnerabilities. Implement image scanning, maintain a secure image registry, and regularly update base images to prevent security compromises.
Cloud Account Hijacking
This is much like thieves stealing your identity to get into your bank account. Attackers get unauthorized access to cloud accounts by stealing credentials. Or they do it by exploiting security gaps. That is why multi-factor authentication should be locked in place. Other suspicious activities should be monitored, and access keys rotated regularly.
Data Breaches and Leakage
Similar to water finding the smallest crack to leak through, sensitive data can escape through overlooked security gaps. This includes accidental exposure and malicious theft. Implement data loss prevention tools, encryption, and regular security assessments to prevent breaches.
Phishing Attacks
Like digital con artists, phishers trick users into revealing login credentials or sensitive information. They often impersonate legitimate services or colleagues. Regular security training, email filtering, and multi-factor authentication help protect against these deceptive attacks.
Misconfigured Cloud Settings
It’s like leaving your security system disabled because it wasn’t set up correctly. Common misconfigurations include public storage buckets or excessive permissions. Regular security assessments, configuration management tools, and automated compliance checking help prevent these issues.
Insider Threats
Sometimes the danger comes from within – like having a dishonest employee with access to valuable assets. Whether malicious or accidental, insider threats can bypass security controls. Monitor user behavior, implement strict access controls, and maintain detailed audit logs.
Brand Reputation Damage and Loss of Customer Trust
Security incidents can shatter customer confidence like breaking a mirror – hard to piece back together. When breaches occur, customers lose trust and your brand suffers. Maintain transparent security practices, prompt incident response, and clear communication protocols.
Business interruption
Security incidents can bring operations to a halt, like a power outage stopping production. Every minute of downtime means lost revenue and productivity. Implement robust business continuity plans, redundant systems, and quick recovery procedures to minimize disruption.
Financial losses
Security breaches hit where it hurts most – your wallet. From immediate recovery costs to long-term reputation damage, the financial impact can be severe. Invest in preventive security measures, maintain cyber insurance, and regularly assess security ROI.
Regulatory Noncompliance
Like driving without following traffic rules, failing to meet security regulations can result in hefty penalties. Different industries and regions have specific compliance requirements. Stay updated with regulations, conduct regular compliance audits, and maintain proper documentation.
Cloud Application Security With Tekrevol to Protect Your Data in the Cloud

We don’t just build cloud applications at Tekrevol; we fortify them. Think of our cloud application development company as your personal cloud security architects who design and implement robust security solutions for your unique needs. Amassed with years of experience in Cloud Security, our team of experts moves well ahead of emerging threats and compliance requirements.
By combining leading technology with industry best practices, we design this comprehensive security framework covering data, applications, and business reputation. From assessment to ongoing monitoring and maintenance, we will be your partner for all the requirements toward maintaining a secure cloud presence.
Final Thoughts
When you don’t leave your house without locking the doors, you can’t afford to leave your cloud applications uncovered in the present digital landscape. As we have explored throughout this guide, cloud application security is not an IT checkbox; it’s a core business strategy that protects the future of your organization.
Remember, the landscape of cloud security is ever-changing; so new threats will always emerge with new technologies. But do not be overwhelmed! By following some best practices we have discussed-from regular backups to comprehensive monitoring-you’re already well on your way to establishing a solid cloud security posture.
Think of cloud security as an ongoing journey rather than a destination. It takes a lot of attention, updates, and improvements, but the investment is well worth it considering the rewards: secure, reliable, and compliant cloud applications.
Regardless of whether you are a novice in your cloud security journey or looking forward to enhancing your security features, remember that you will never have to go alone. With the right collaborator and proper security applied, you can harness the power that comes with cloud computing right in the comfort of assured security for data and their respective businesses.
Want your cloud security to be raised one more notch? Let’s create a safer future with the right measures to engage your business on another platform.

 599 Views
599 Views January 17, 2025
January 17, 2025






