Imagine this: a user downloads your app, entrusting it with their sensitive information, only to find out it’s vulnerable to hackers. Alarming, right? In 2025, this is more than a hypothetical scenario—it’s a growing reality as cyberattacks on mobile apps surged by 80% last year, targeting apps of all sizes.
In a world with 7 billion mobile users, app security is essential. Ignoring it can lead to data breaches, erode user trust, and damage your brand’s reputation.
According to ASEE, 75% of mobile apps suffer from security vulnerabilities. So, how can you ensure your app is ready to meet these challenges head-on?
This blog we will walk you through how you can avoid common pitfalls and secure your app effectively.
The Alarming Rise in Mobile App Threats
Cyber threats targeting mobile applications are on the rise at an alarming rate. You should know that approximately four out of five mobile applications have at least one vulnerability. And data breaches have skyrocketed by an astonishing 54% within the same duration of one year alone.
It is becoming more difficult for application developers to prevent attackers from reverse engineering, injecting code, and employing malware tools. These attacks not only involve the theft of user data but also undermine confidence and can greatly affect the reputation of any brand. This is a wake-up call for developers & businesses to step up their game to ensure that the apps in their businesses are as secure as ever before.
Global Data Regulations: How They Impact Your Business Operations
As the threat of data breaches grows, regulatory bodies enforce stricter privacy laws on businesses. Ignoring these costs more than just heavy fines-it can damage your reputation. That is why complying should be at the very top. Here’s an overview of the major regulations and how they impact businesses.
| Aspect | Details | Impact on Business |
| GDPR (Europe) | Requires explicit user consent for data collection and imposes fines up to €20M or 4% of revenue. | Non-compliance can result in legal penalties and loss of customer trust. |
| CCPA (U.S.) | Empower consumers to control their personal data with the right to opt out of data sharing. | Failing to comply can lead to lawsuits and damage to the brand’s reputation. |
| Future Regulations (2025) | Expected to include more stringent rules around data encryption and user consent. | Businesses must proactively adopt robust security measures to stay ahead of legal changes. |
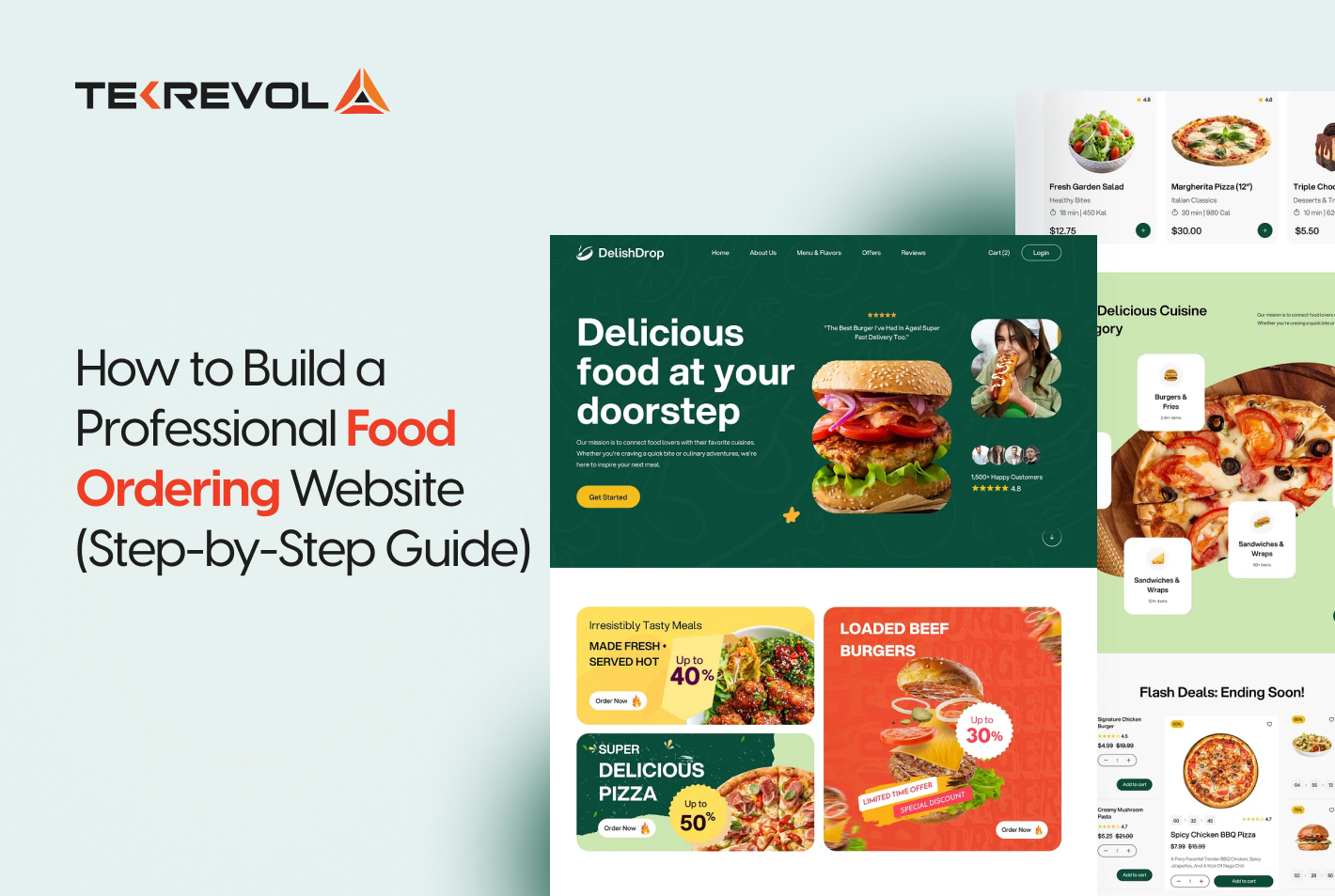
Top Mobile Security Challenges Your Organization Must Address
Smartphones and tablets are vital resources in today’s organizations, but they are also an appealing target for hackers. The use of mobile applications, combined with the adoption of cloud services, increases the dangers for businesses. The most serious mobile risks are listed here, along with statistics and examples to demonstrate their impact.
1. Mobile Phishing (Mishing)
A mobile version of phishing is the use of deceptive methods to obtain users’ data. Next, it’s important to note that mobile audiences are also at higher risk because they use smaller devices with limited visibility of non-text content and heavily rely on messaging apps.
Statistics:
- A composable study shows that 82% of the phishing websites created are exclusive to mobile users.
- It is significant that 25% of users clicked at least one phishing link each quarter in 2023.
Real-Life Example:
The 2022 smishing attack took the shape of an SMS pretending to be from the logistics business DHL. Customers were notified of the delivery of their orders by email and asked to visit a link. The link created by the crooks gathered financial credentials from thousands of clients worldwide.
How to Mitigate:
- Make the employees familiar with how to recognize phishing emails.
- Mobile security solutions should incorporate anti-phishing mechanisms.
- Try controlling the occurrence of suspicious links on corporate devices.
2. Mobile Malware
Mobile malware therefore is classified as viruses, trojans, ransomware, and spyware among others that target and seek to take advantage of the loopholes in mobile devices. It usually enters a device through dangerous sites, untrustworthy apps, or even risky ads.
Statistics:
- Security experts estimated that 5.5 million users installed high-risk applications on Google Play Store in 2023.
- The average ransom in 2024 is $2.73 million, almost an increase of $1 million from 2023. (Sophos)
Real-Life Example:
Despite strict security measures, the Joker malware repeatedly slipped into the Google Play Store, posing as legitimate apps like photo editors and wallpaper tools. By quietly enrolling users in unauthorized services, led to millions of dollars in fraudulent charges across the globe.
How to Mitigate:
- Deploy app vetting policies.
- Employ solutions that detect endpoints to monitor devices.
- Always ensure that one has the latest version of the operating systems and other related applications.
3. Side-loaded Apps
Side loading means loading applications from other sources apart from the Android Market, Apple App Store, and any other formal market. It may seem very convenient to have apps installed this way but it means that the apps can be installed without going through official channels and checks.
Statistics:
- Side-loading apps are used by 18% of users.
- Sideloaded apps are 47% more likely to have at least one form of malware than those apps downloaded from official stores.
Real-Life Example:
An Employee at a European bank took advantage of the organization’s ends and sideloaded an unverified app to track cryptocurrency prices in 2021. The spyware was installed in the application through which personal information belonging to customers was retrieved from the companies’ databases.
How to Mitigate:
- Prohibit side-loading on work devices by enforcing strict policies against the activities.
- Detect applications installed without permission with the help of MDM tools for controlling devices.
4. Platform Vulnerabilities
Mobile platforms like Android and iOS continuously update their versions to patch security holes. However, most users do not update their devices, leaving them vulnerable to known exploits. An unpatched vulnerability is an open door for cybercriminals.
Statistics:
- Old software, which is already known for its security holes, is used on 40% of mobile devices.
- About 500 million Android devices were left unpatched in 2022.
Real-Life Example:
The Stagefright vulnerability in Android enabled attackers to seize control over the devices by sending a dangerous multimedia message. This weakness was taken advantage of in millions of devices before the release of the patches.
How to Mitigate:
- Ensure that relevant policies are implemented to ensure the information is updated frequently.
- User updates must be managed through MDM and these updates must also be automated.
- Upgrade to a newer operating system, and remove support from old devices that have not been officially updated.
5. Poorly Vetted Applications
Applications, whether in-house or third-party, are also a significant source of risk if they have not been vetted properly. An application with poor security practices can introduce vulnerabilities that put sensitive data at risk.
Statistics:
- According to the research, more than half of mobile apps contain a variety of major security vulnerabilities.
- Over 75% of mobile applications are reported to neglect simple security measures, such as password protection for storing data.
Real-Life Example:
In 2023, a multinational company’s fitness application lacked encryption, which was an example of a violation of user data. Criminals were able to exploit it and gain access to users’ personal information, including GPS location and staff health information, exposing millions of people to privacy violations.
How to Mitigate:
- Perform deep security assessments of third-party applications.
- Another protection measure that can be advised is to limit the extent of permissions given to the applications.
- Apply security coding and guidelines and test in-house applications consistently.
The Future of Mobile App Security: 2025 Security Strategies

To remain competitive by 2025, firms will need to adjust to new threats and technological advancements. These are the main forecasts influencing how mobile app security will develop in the future:
-
Ensuring Secure Environments for Critical Apps
App makers are changing their approach to dealing with device integrity mainly out of security concerns. Traditionally, checks such as root detection were resisted because they were seen as being inconvenient. Financial and identity-based apps are now changing this.
For instance, applications for digital banking and SoftPOS must comply with PCI standards, which require apps to run only on verified, secure devices. This is important for compliance and building customer confidence.
Other applications using identity confirmation, including KYC with face recognition, are also tightening measures against fraud. High-risk industries will experience a rise in device integrity mandates by 2025.
-
Enhanced Malware Defenses in Mobile Apps
Phishing attempts that use social engineering techniques are increasingly being used to distribute mobile malware that targets the Android platform. Even though phishing education is crucial, app developers are taking a risk by blocking attack strings like Accessibility Services APIs and overlays.
Attackers are highly capable of utilizing user devices, and developers are increasingly incorporating detection tools and restricting APIs.
For instance, apps in the finance and healthcare domains are increasingly incorporating robust malware safeguards to guard their information assets. By 2025, such measures will increase the difficulty for attackers, minimizing the effects of malware campaigns.
-
Dynamic Security Models for Adaptive Protection
While threats are becoming more diverse, developers are gradually shifting from using traditional forms of static security to dynamic ones based on policies. Updates that occur dynamically using server-side attestation make it possible for apps to change security parameters without necessarily the user or an update in the app.
This technique improves tamper resistance by allowing for the real-time adjustment of new malware patterns and redesigning allow-list policies.
For example, financial apps can alter their security features as threats evolve, ensuring their safety at all times. In 2025, these adaptable models will offer developers an efficient competitive strategy for securing their applications.
-
User-Friendly Security Tools for Developers
A talent shortage in mobile security has led to the increased need for affordable solutions to tackle the problem. According to the report “Assessing Mobile Application Security,” 71% of organizations admitted to having a security skills gap.
However, nearly 98% are actively buying or planning to buy extra security solutions to help bridge that gap. The only downfall is that not all those security solutions are tailored specifically for developers.
To fill up this gap, there are tools like OWASP MASv2 and the Mobile Application Security Testing Guide that are easing the implementation of security. Further, vendors are inventing solutions that allow any developer to implement subprocessors’ security measures successfully.
All these tools will enable developers to secure applications in the future without affecting their usability by 2025 making applications secure for everyone.
- Are you confident in your app's security?
- TekRevol can help strengthen your defenses against threats.
- Book a Consultation Today!
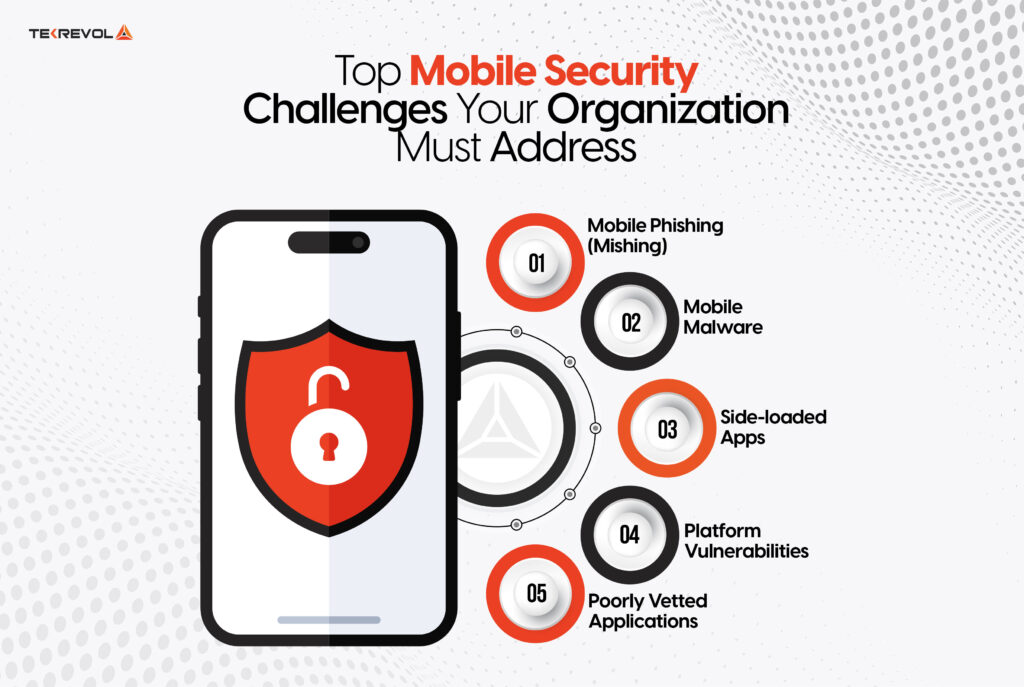
Best Practices for Enhancing iOS App Security
iOS app security is something that app developers should consider and take action on as early as possible. Here’s a structured breakdown of essential practices:
1. Protect User Data with Encryption
It is important to have a very high level of data security when it comes to storing material such as passwords or credit card numbers. Utilize tools such as CryptoSwift to encrypt data through AES and even add a grain of additional non-standard salt to hash functions. This ensures that even if data reaches a third party or unauthorized person, they cannot understand it.
2. Validate App Integrity
Code signing is a necessity for iOS applications and their identification passes through the strict examination by Apple. Strengthen this further by applying runtime verification to dynamic link libraries. This gives a certain assurance that your App has not been modified in any way after development.
3. Streamline Permissions
Each permission required should have a nice-sounding purpose. Check your app and find out that it requires permissions it does not need. This approach lowers risks while increasing the trust of its users about their data.
4. Enable SSL Pinning
Man-in-the-middle attacks are considered to be a problem that does not go away. Deal with SSL pinning which serves as a security feature preventing communication with any server that uses a certain certificate. This prevents unauthorized parties from injecting or modifying information meant to be transferred between systems.
5. Biometric Authentication
Add Face ID or Touch ID so that the user has an added layer of protection. Biometrics with Keychain for a secure and multiple-factor identification process that will guarantee user’s information is well protected.
- Need expert help with iOS app security?
- TekRevol’s team has the experience and tools to keep your app safe.
- Get in touch today!
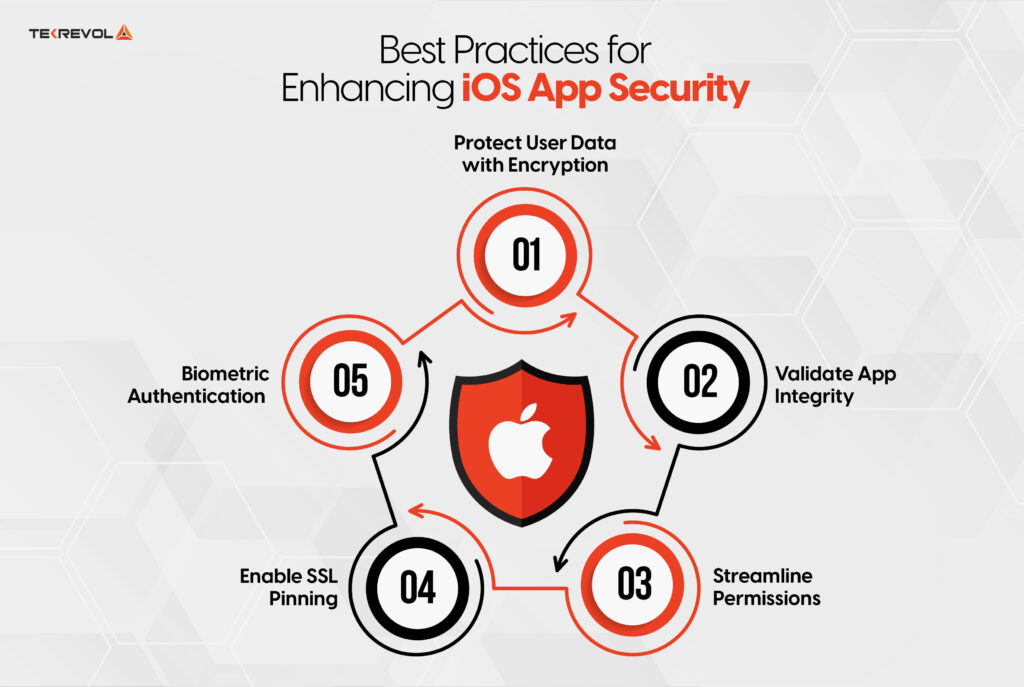
Best Practices for Enhancing Android App Security
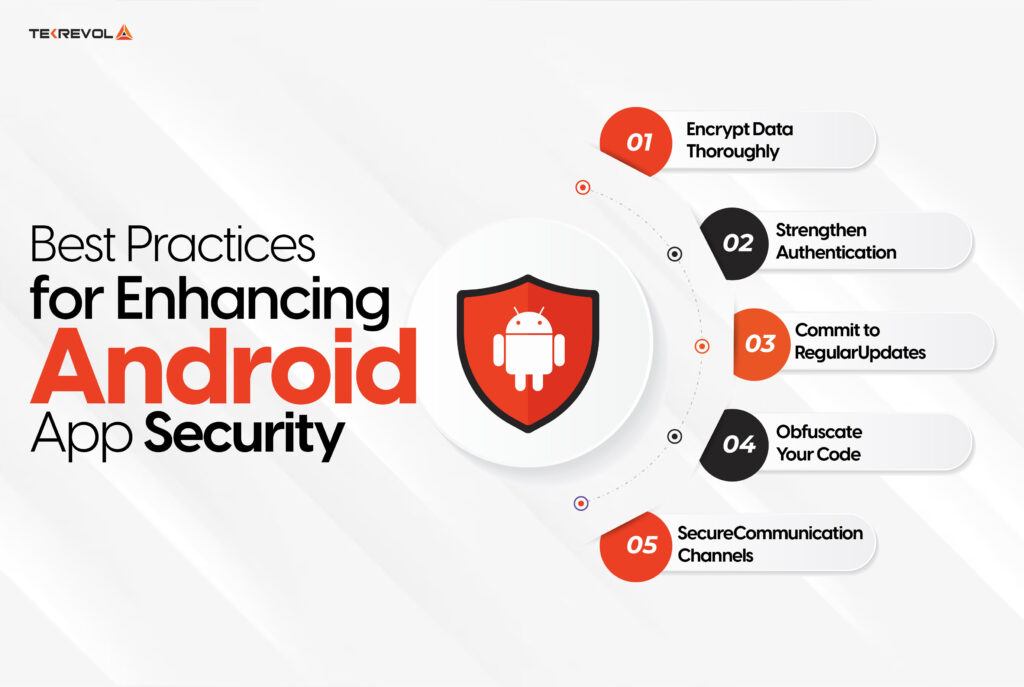
Android app security in particular is achieved both through careful planning and constant refinement. Follow these structured steps to safeguard your app and users:
1. Encrypt Data Thoroughly
Use the AES-256 encryption both on data that is stored in the system and on data transmitted through the system. Modern technologies like BouncyCastle help prevent unauthorized access to users’ credentials and other Personal Identifiable Information.
2. Strengthen Authentication
Implement multi-factor authentication (MFA) because one form of identification is not enough to grant the user access. Introduce biometrics and OTPs for further security measures. The best way to implement the login methods is by integrating OAuth protocols required in applications dealing with sensitive data.
3. Commit to Regular Updates
Always be careful with security patches. Keep an eye and track on which part of your app code is vulnerable, or which of the third-party libraries used are actually a problem. This provides our defense system with the latest updated threats to help counter and prevent the attacks.
4. Obfuscate Your Code
Avoid reverse development by hiding your app’s code. Code-shrinking libraries like ProGuard or R8 complicate the reversal process and thus prevent you from sharing your ideas or intellectual property with the attackers.
5. Secure Communication Channels
Use HTTPS for all the server communications and adopt SSL/TLS pinning for server certifications. This prevents the attackers to pretend as clueless servers or get in-between your files while they are being transferred.
Protect Your Apps with TekRevol’s Advanced Security Solutions
As the threat of cyber attacks unfolds in 2025, mobile app security is seen as a critical area of interest by developers and entrepreneurs alike. Being a leading mobile app development company in Chicago, we incorporate security measures at the initial stages of constructing your applications so that your applications are protected from these new threats.
Security also doesn’t end with the deployment. We immediately implement updates and patches to seal any loophole the new threats may target. Our team is always on the watch to monitor your app environment to guard your apps, users’ data, and other resources. This commitment to post-launch security is a factor in maintaining user’s trust and satisfaction.
We act as a role model when it comes to cybersecurity. To kick off 2025, our specialists have the capability of offering secure, stable, and engaging experiences. With TekRevol, you can explore the digital world like never before with the assurance that your app is safeguarded against emerging dangers.
- Worried about safeguarding your app and user data?
- Get Advanced security solutions with TekRevol that build trust and protect your users.
- Book A Free Call Now!





![How Much Would It Truly Cost to Develop a Food Ordering Website? [2026 Analysis]](https://d3r5yd0374231.cloudfront.net/images-tek/uploads/2026/03/Tek-Feature-7-1.jpg)